环境要求
vmware虚拟机双核2G内存以上
安装有CentOS7和docker
配置nginx图片防盗链
配置盗链网站
1) 启动nginx容器,设置端口映射,并进入容器docker run -d --privileged -p 80:80 -p 443:443 nginx /usr/sbin/init
2) 在nginx容器中准备两个网站,配置文件1
2
3
4
5
6
7
8
9
10
11
12server {
listen 80;
server_name site1.test.com;
root /var/www/html/site1;
index index.html;
}
server {
listen 80;
server_name site2.test.com;
root /var/www/html/site2;
index index.html;
}
3) 在主机编辑hosts文件1
2虚拟机的IP地址 site1.test.com
虚拟机的IP地址 site2.test.com
4) 创建/var/www/html/site1/index.html,展示自己的图片1
2<h1>welcome to site1</h1>
<img src=”1.jpg”>
从网上随便下载一张图片作为1.jpgwget https://www.heuet.edu.cn/images/18/03/07/2tf9v0vlbb/20150415094513422.jpg
5) 创建/var/www/html/site2/index.html,盗用site1的图片1
2<h1>welcome to site2</h1>
<img src=”http://site1.test.com/1.jpg”>
1 | [root@5ef46ce6b610 /]# mkdir -p /var/www/html/site1 |
重启nginx服务systemctl restart nginx
6) 在主机浏览器访问site1.test.com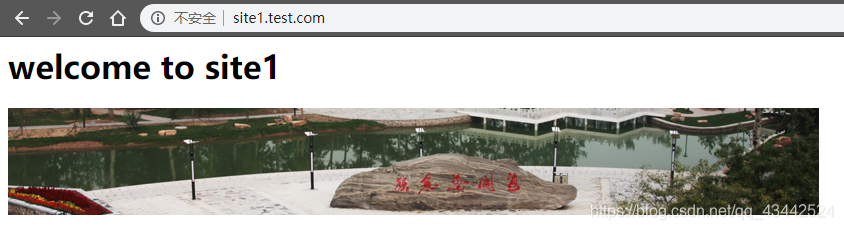
7) 在主机浏览器访问site2.test.com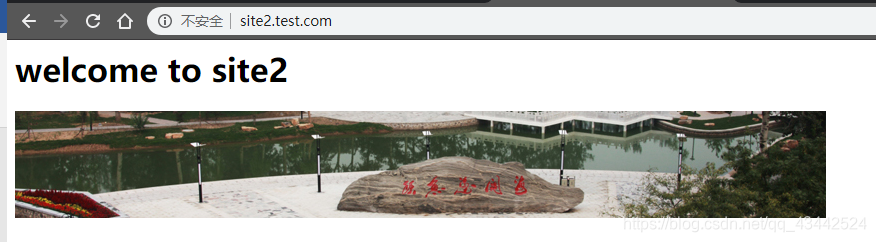
配置site1.test.com防盗链
1) 在nginx容器中编辑/etc/nginx/nginx.conf文件,配置防盗链
配置两台虚拟主机1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25 server {
listen 80;
server_name site1.test.com;
location / {
root /var/www/html/site1;
index index.html index.htm;
}
location ~ \.(jpg|png|gif)$ {
valid_referers site1.test.com;
if ($invalid_referer) {
return 403;
}
}
}
server {
listen 80;
server_name site2.test.com;
location / {
root /var/www/html/site2;
index index.html index.htm;
}
}
说明:
判断referer的值,来判断当前图片的引用是否合法,一旦检测到来源不是本站,就立即阻止图片的发送,或换成一张禁止防盗链提示的图片1
2
3
4
5
6location ~ \.(jpg|png|gif)$ {
valid_referers site1.test.com;
if ($invalid_referer) {
return 403;
}
}
- 第1行配置,用于匹配文件扩展名为gif、jpg、png、swf、flv的资源
- 第2行中的
valid_referers指令用于设置允许访问资源的网站列表(即白名单)。当请求消息头中的referer符合白名单时,内置变量$invalid_referer的值为空字符串,否则为1 - 第3~5行的配置,可以禁止白名单之外的网站访问资源,并返回403状态码
2) 在主机使用浏览器访问site1.test.com
3) 在主机使用浏览器访问site2.test.com
如果测试仍然显示图片,是因为浏览器还有上次访问的缓存
建议更换浏览器,或者清理缓存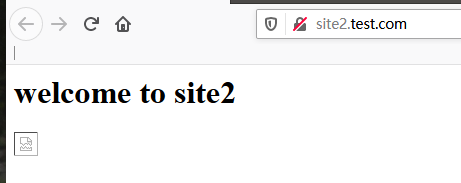
配置nginx的HTTPS网站
颁发网站认证证书
1) 在nginx容器中检查系统安装了openssl1
2
3
4[root@5ef46ce6b610 site1]# rpm -qa | grep ssl
openssl-libs-1.1.1c-2.el8.x86_64
openssl-1.1.1c-2.el8.x86_64
[root@5ef46ce6b610 site1]#
2) 建立/etc/nginx/ssl目录,并生成服务器RSA私钥openssl genrsa -out server.key 2048
1 | [root@5ef46ce6b610 site1]# mkdir /etc/nginx/ssl |
3) 生成服务器CSR证书请求文件,注意站点名称要一致
openssl req -new -key server.key -out server.csr1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41[root@5ef46ce6b610 ssl]# openssl req -new -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Hebei
Locality Name (eg, city) [Default City]:Shijiazhuang
Organization Name (eg, company) [Default Company Ltd]:It
Organizational Unit Name (eg, section) []:www.test.com
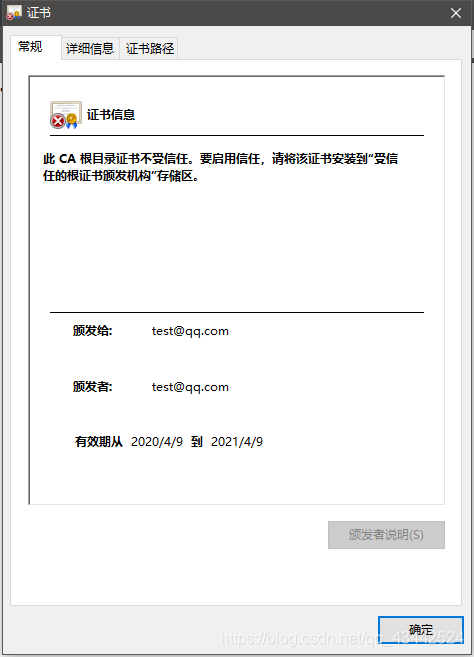
Common Name (eg, your name or your server's hostname) []:test@qq.com
Email Address []:test@qq.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@5ef46ce6b610 ssl]# ls
server.csr server.key
[root@5ef46ce6b610 ssl]# cat server.csr
-----BEGIN CERTIFICATE REQUEST-----
MIIC0DCCAbgCAQAwgYoxCzAJBgNVBAYTAkNOMQ4wDAYDVQQIDAVIZWJlaTEVMBMG
A1UEBwwMU2hpamlhemh1YW5nMQswCQYDVQQKDAJJdDEVMBMGA1UECwwMd3d3LnRl
c3QuY29tMRQwEgYDVQQDDAt0ZXN0QHFxLmNvbTEaMBgGCSqGSIb3DQEJARYLdGVz
dEBxcS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCZ/NmYb3Wy
WrxrkI1o0XbxAVLIHGHgA7rO1MLMqk9ejEI0A2bwGeZYt3cQjAFkJhaHolSt9zwf
FMBNtbIfDQqoTqsQOW6LXluD1yu27XGsPxchumD+7N8MN6aD16/F1epDg+NxuiPF
GSS4oXw5LJobfxnwrQV31ldttfgfLSsaEOs8hvJZxkF84fhXoyk8QzvTenvJ8Y53
9MDHP2P1OBOPyHOxMvWoYfP+DzHvk6T5K6SaWfpzeb1WrZbkSI3Sij+4Uka+zdCa
IXvBtYB0UU5OeMnsLpdgWbOLMjqg0JKF6BAyCgpnYbh9OeJ2c0oP2AqfxDPcdZN/
tjpUx+WpjdjZAgMBAAGgADANBgkqhkiG9w0BAQsFAAOCAQEAGTlfc6+S5ptsyJ47
lN8+neD6+9wX+5zomp3TUHbikSAdUvwNHnZJb2M3Mrg5q+Lde9MLj0W3rlVNx8Sr
4OMVvO/f/C/cUp0r6Qn2RRUtP9HRCthuQTP+61cXr8WUpOjcbnr6VE2tJ285KdU2
uR9ODTwfl5iP6hwyBlXLkDohhDuGAYlEL93yt3OzCTddeVFqklhD5cAlWX3s+pqm
Xzv70KUy68rCL1YDjgXX6u6QZ+63z+pmQoXv/Bk6JYUAqalKeeQH/VtHGwaJ6UuP
QF40i8ffeFuk8ZmgCB1jm57MPR1oyorgI72063wE6cvrf0OLFSCJfufyab5mvzV/
bNjXbQ==
-----END CERTIFICATE REQUEST-----
4) 生成服务器认证证书openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
1 | [root@5ef46ce6b610 ssl]# openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt |
配置HTTPS网站
1) 在主机编辑hosts文件,并使用ping命令检查
虚拟机的IP地址 www.test.com
2) 编辑/etc/nginx/nginx.conf文件,配置HTTPS站点1
2
3
4
5
6
7
8
9
10
11server {
listen 443;
server_name www.test.com;
root /var/www/html;
ssl on;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
index index.html;
}
}
3) 编辑 /var/www/html/index.html,重载nginx1
<h1>this is https site!!</h1>
systemctl restart nginx
4) 重载nginx,在主机使用浏览器访问 https://www.test.com
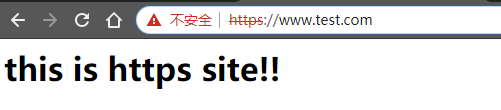
5) 在浏览器中查看网站证书,