上节讲解了通过kubeadm 搭建集群kubeadm1.15.1环境,现在的集群已经搭建成功了,今天给大家展示Kubernetes Dashboard 插件的安装
下载官方的yaml文件
进入官网:https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/1
$ wget https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
修改:
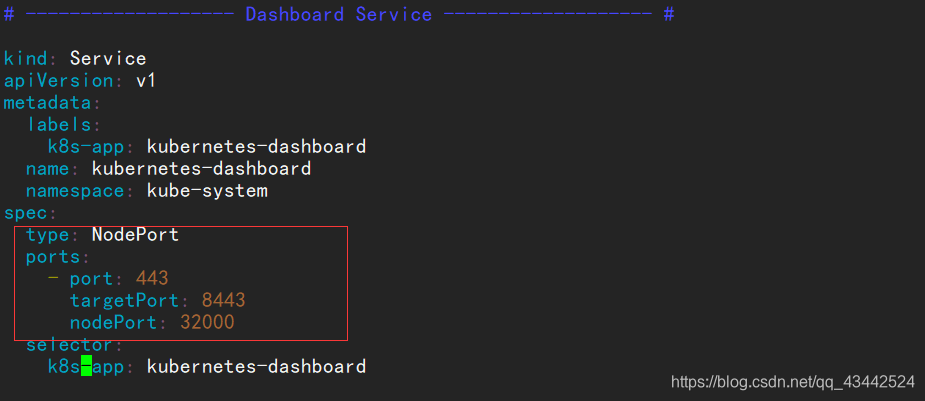
type,指定端口类型为 NodePort,这样外界可以通过地址 nodeIP:nodePort 访问 dashboard
如果网络不好,不能直接下载,需要手动创建kubernetes-dashboard.yaml文件1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
# ------------------- Dashboard Secret ------------------- #
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
# ------------------- Dashboard Role & Role Binding ------------------- #
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret.
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
# Allow Dashboard to create 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
# ------------------- Dashboard Deployment ------------------- #
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
# ------------------- Dashboard Service ------------------- #
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 32000
selector:
k8s-app: kubernetes-dashboard
拉取镜像
为了避免访问外国网站,这里直接通过国内的阿里镜像拉取,通过tag更改名称1
2docker pull registry.cn-hangzhou.aliyuncs.com/rsqlh/kubernetes-dashboard:v1.10.1
docker tag registry.cn-hangzhou.aliyuncs.com/rsqlh/kubernetes-dashboard:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
1 | [root@k8s-node01 ~]# docker pull registry.cn-hangzhou.aliyuncs.com/rsqlh/kubernetes-dashboard:v1.10.1 |
部署yaml文件
通过kubectl create -f命令部署1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23[root@k8s-master01 ui]# kubectl create -f kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[root@k8s-master01 ui]# kubectl get pod -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-5c98db65d4-54j5c 1/1 Running 0 3h53m
coredns-5c98db65d4-jmvbf 1/1 Running 0 3h53m
etcd-k8s-master01 1/1 Running 2 10d
kube-apiserver-k8s-master01 1/1 Running 2 10d
kube-controller-manager-k8s-master01 1/1 Running 3 10d
kube-flannel-ds-amd64-6h79p 1/1 Running 2 9d
kube-flannel-ds-amd64-bnvtd 1/1 Running 3 9d
kube-flannel-ds-amd64-bsq4j 1/1 Running 2 9d
kube-proxy-5fn9m 1/1 Running 1 9d
kube-proxy-6hjvp 1/1 Running 2 9d
kube-proxy-t47n9 1/1 Running 2 10d
kube-scheduler-k8s-master01 1/1 Running 4 10d
kubernetes-dashboard-7d75c474bb-zj9c6 1/1 Running 0 18s
[root@k8s-master01 ui]#
可以看到kubernetes-dashboard处于Running状态1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20[root@k8s-master01 ui]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 10d
kubernetes-dashboard NodePort 10.110.65.174 <none> 443:32000/TCP 11m
[root@k8s-master01 ui]# kubectl get pod -n kube-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
coredns-5c98db65d4-54j5c 1/1 Running 0 4h5m 10.244.2.5 k8s-node02 <none> <none>
coredns-5c98db65d4-jmvbf 1/1 Running 0 4h6m 10.244.1.5 k8s-node01 <none> <none>
etcd-k8s-master01 1/1 Running 2 10d 192.168.0.50 k8s-master01 <none> <none>
kube-apiserver-k8s-master01 1/1 Running 2 10d 192.168.0.50 k8s-master01 <none> <none>
kube-controller-manager-k8s-master01 1/1 Running 3 10d 192.168.0.50 k8s-master01 <none> <none>
kube-flannel-ds-amd64-6h79p 1/1 Running 2 9d 192.168.0.52 k8s-node02 <none> <none>
kube-flannel-ds-amd64-bnvtd 1/1 Running 3 9d 192.168.0.50 k8s-master01 <none> <none>
kube-flannel-ds-amd64-bsq4j 1/1 Running 2 9d 192.168.0.51 k8s-node01 <none> <none>
kube-proxy-5fn9m 1/1 Running 1 9d 192.168.0.51 k8s-node01 <none> <none>
kube-proxy-6hjvp 1/1 Running 2 9d 192.168.0.52 k8s-node02 <none> <none>
kube-proxy-t47n9 1/1 Running 2 10d 192.168.0.50 k8s-master01 <none> <none>
kube-scheduler-k8s-master01 1/1 Running 4 10d 192.168.0.50 k8s-master01 <none> <none>
kubernetes-dashboard-7d75c474bb-zj9c6 1/1 Running 0 13m 10.244.1.6 k8s-node02 <none> <none>
[root@k8s-master01 ui]#
可以看到kubernetes-dashboard暴露在node2上的32000端口
访问ui页面
https://192.168.0.52:32000/ 这是我node2的ip地址
建议使用firefox访问, Chrome访问会禁止不安全证书访问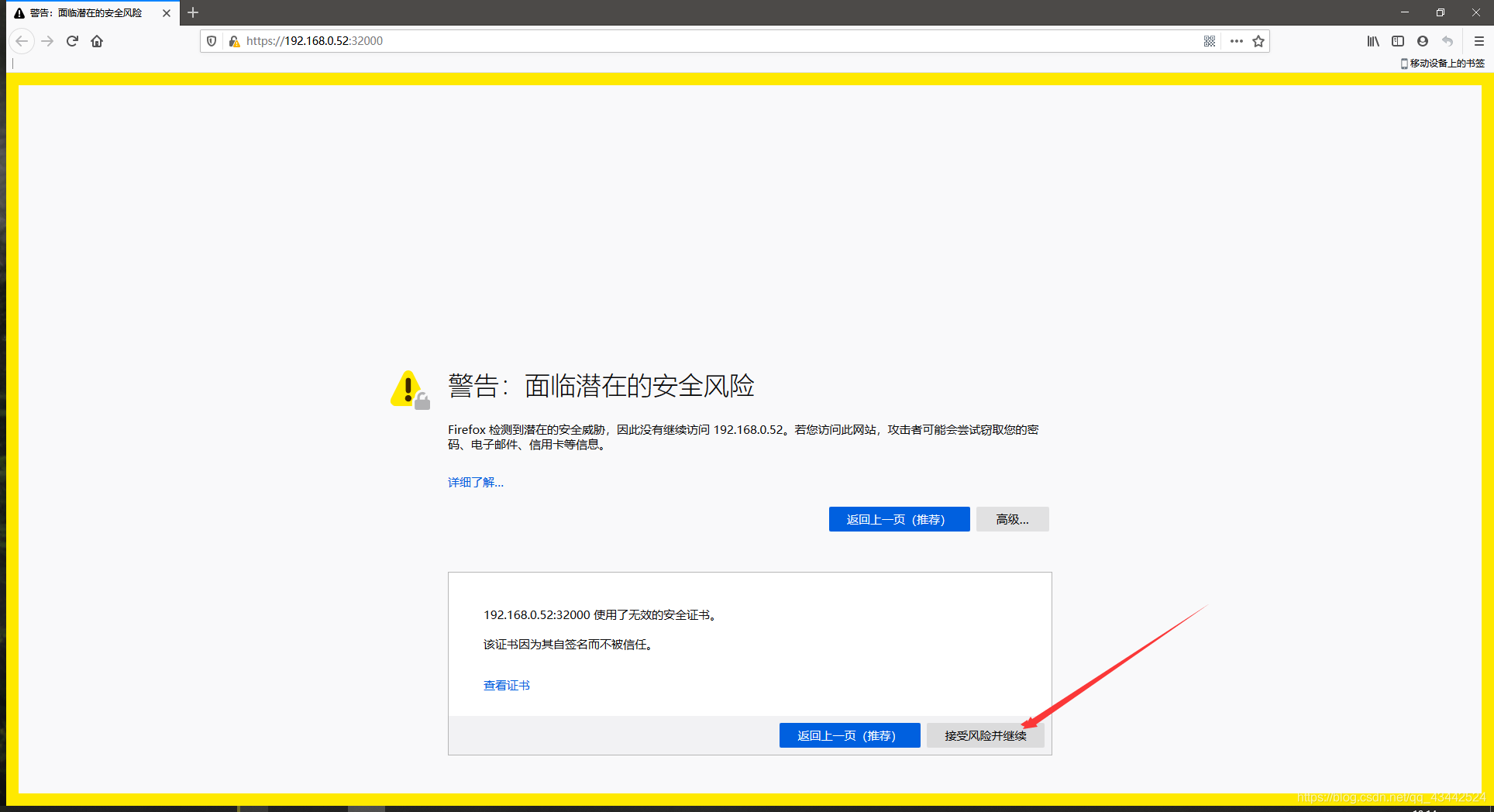
Token令牌登录
- 创建serviceaccount
kubectl create serviceaccount dashboard-admin -n kube-system1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38[root@k8s-master01 ~]# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
[root@k8s-master01 ~]# kubectl get sa -n kube-system
NAME SECRETS AGE
attachdetach-controller 1 10d
bootstrap-signer 1 10d
certificate-controller 1 10d
clusterrole-aggregation-controller 1 10d
coredns 1 10d
cronjob-controller 1 10d
daemon-set-controller 1 10d
dashboard-admin 1 27s
default 1 10d
deployment-controller 1 10d
disruption-controller 1 10d
endpoint-controller 1 10d
expand-controller 1 10d
flannel 1 10d
generic-garbage-collector 1 10d
horizontal-pod-autoscaler 1 10d
job-controller 1 10d
kube-proxy 1 10d
kubernetes-dashboard 1 48m
namespace-controller 1 10d
node-controller 1 10d
persistent-volume-binder 1 10d
pod-garbage-collector 1 10d
pv-protection-controller 1 10d
pvc-protection-controller 1 10d
replicaset-controller 1 10d
replication-controller 1 10d
resourcequota-controller 1 10d
service-account-controller 1 10d
service-controller 1 10d
statefulset-controller 1 10d
token-cleaner 1 10d
ttl-controller 1 10d
[root@k8s-master01 ~]#
dashboard-admin 1 27s创建成功
- 把serviceaccount绑定在clusteradmin,授权serviceaccount用户具有整个集群的访问管理权限
1
kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
1 | [root@k8s-master01 ~]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin |
- 获取serviceaccount的secret信息,可得到token(令牌)的信息
kubectl get secret -n kube-system
dashboard-admin-token-slfcr 通过上边命令获取到的kubectl describe secret dashboard-admin-token-slfcr -n kube-system1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53```bash
[root@k8s-master01 ~]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
attachdetach-controller-token-j5vtc kubernetes.io/service-account-token 3 10d
bootstrap-signer-token-prjr2 kubernetes.io/service-account-token 3 10d
certificate-controller-token-f8rjx kubernetes.io/service-account-token 3 10d
clusterrole-aggregation-controller-token-l6lqh kubernetes.io/service-account-token 3 10d
coredns-token-p5z2z kubernetes.io/service-account-token 3 10d
cronjob-controller-token-jsp8k kubernetes.io/service-account-token 3 10d
daemon-set-controller-token-4fh89 kubernetes.io/service-account-token 3 10d
dashboard-admin-token-dl8pf kubernetes.io/service-account-token 3 9m2s
default-token-22jpc kubernetes.io/service-account-token 3 10d
deployment-controller-token-jc4xc kubernetes.io/service-account-token 3 10d
disruption-controller-token-p85cv kubernetes.io/service-account-token 3 10d
endpoint-controller-token-dhk4f kubernetes.io/service-account-token 3 10d
expand-controller-token-lbsrj kubernetes.io/service-account-token 3 10d
flannel-token-qjgks kubernetes.io/service-account-token 3 10d
generic-garbage-collector-token-6fwmg kubernetes.io/service-account-token 3 10d
horizontal-pod-autoscaler-token-vl8dh kubernetes.io/service-account-token 3 10d
job-controller-token-c2sfm kubernetes.io/service-account-token 3 10d
kube-proxy-token-qg465 kubernetes.io/service-account-token 3 10d
kubernetes-dashboard-certs NodePort 0 56m
kubernetes-dashboard-key-holder Opaque 2 56m
kubernetes-dashboard-token-hpg2q kubernetes.io/service-account-token 3 56m
namespace-controller-token-vvbxk kubernetes.io/service-account-token 3 10d
node-controller-token-5hmv6 kubernetes.io/service-account-token 3 10d
persistent-volume-binder-token-6vrk6 kubernetes.io/service-account-token 3 10d
pod-garbage-collector-token-f8bvl kubernetes.io/service-account-token 3 10d
pv-protection-controller-token-pp8bh kubernetes.io/service-account-token 3 10d
pvc-protection-controller-token-jf6lj kubernetes.io/service-account-token 3 10d
replicaset-controller-token-twbw8 kubernetes.io/service-account-token 3 10d
replication-controller-token-lr45r kubernetes.io/service-account-token 3 10d
resourcequota-controller-token-qlgbb kubernetes.io/service-account-token 3 10d
service-account-controller-token-bsqlq kubernetes.io/service-account-token 3 10d
service-controller-token-g6lvs kubernetes.io/service-account-token 3 10d
statefulset-controller-token-h6wrx kubernetes.io/service-account-token 3 10d
token-cleaner-token-wvwbn kubernetes.io/service-account-token 3 10d
ttl-controller-token-z2fm7 kubernetes.io/service-account-token 3 10d
[root@k8s-master01 ~]# kubectl describe secret dashboard-admin-token-dl8pf -n kube-system
Name: dashboard-admin-token-dl8pf
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: b4fc67f6-1cab-4486-8652-05346c939c6d
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tZGw4cGYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiYjRmYzY3ZjYtMWNhYi00NDg2LTg2NTItMDUzNDZjOTM5YzZkIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.ArAKoKEiZ0xaV9rqff63iq2t6iAsWBmA-VhHKK_pnkiMObpPL-JjZras40HO0crE7Gnou9dUWCStW3AbfmtJ1SX_Hmo4OlXGH2xFBJ-_2wruwWOU89dlHhOnhw8__skhsVrE92-KDK00GRSrA4BkUu8PWp45jCQyIwFbF8h3L2ydcNlcs_rxGieVFRc1p9gaf_HAyXIIHEgu-M5LxA6BduN-3Z7WBzYMokFd_r_c_beAQ4CUlTYc1c0FjmqLeyZpyLJL6IMqztjaYHFXiRty6c-PQHZd6HQoElJShbw1lhZtHXSSw0A70Kb3ZVfqQZxRaOsqJYo70sZXQQRaYso6fg
[root@k8s-master01 ~]#
输入Token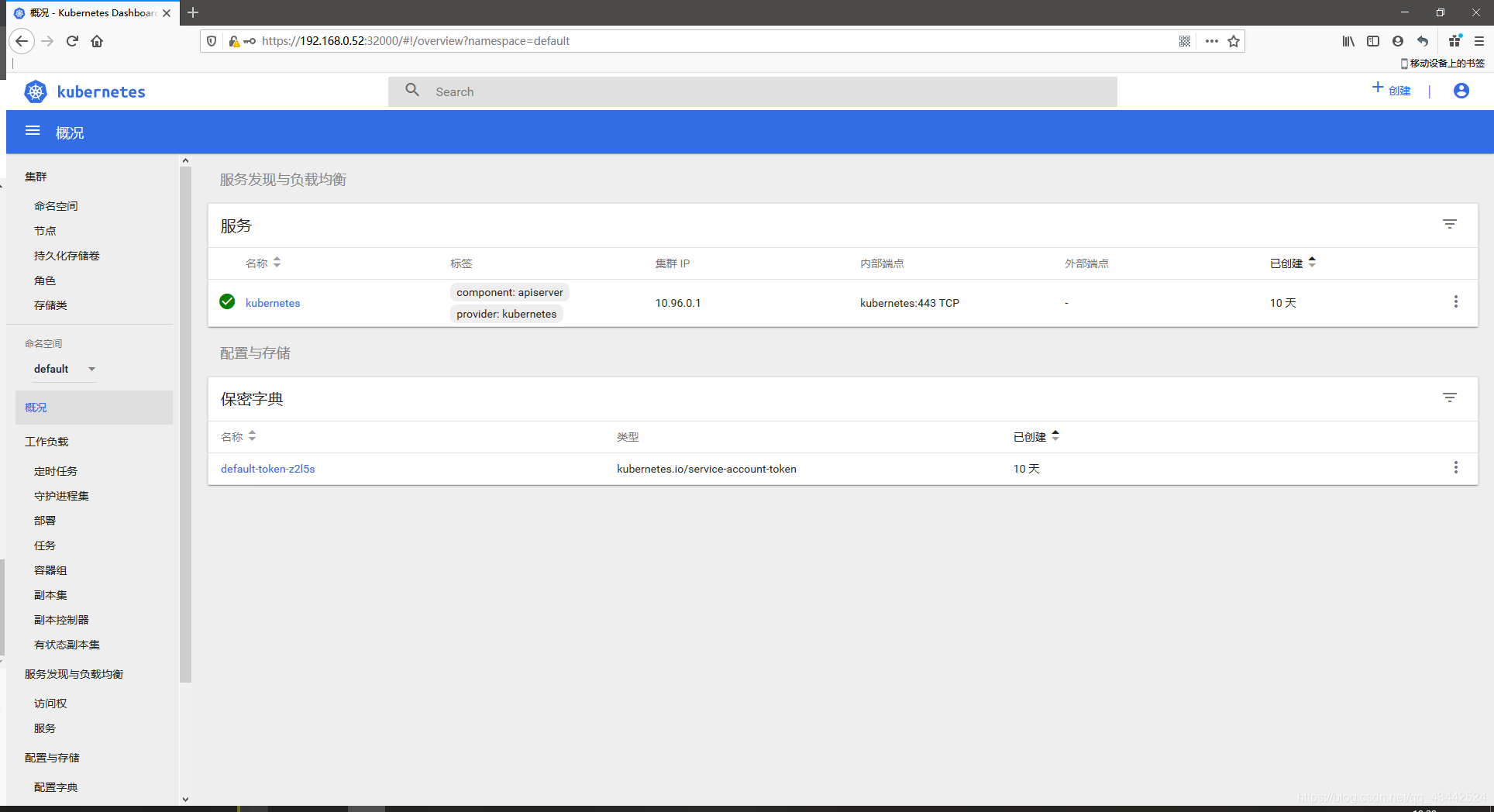
部署成功!